Uni-cast, Broadcast, and Multicast in Computer Networks
Uni-cast, Broadcast, and Multicast in Computer Networks
Introduction
The numerous protocols and technologies used in computer networks make it possible for devices to effectively communicate with one another and transmit data. For example, Local area networks (LAN's) that use wired connections must adhere to the requirements of Ethernet, a widely used technique. Wi-Fi enables wireless device connections without the use of wires by using radio waves to transmit data. Bluetooth allows devices to communicate wireless across short distances.
The protocols TCP/IP, HTTP/HTTPS, and FTP enable dependable file transmission, web surfing, and communication via networks. Email communication is handled by the SMTP/POP/IMAP protocols. Domain names are converted into IP addresses via DNS. Along with several other techniques, Computer network’s communication modes, Unicast, multicast, and broadcast, lay the groundwork for effective and secure communication within computer networks, facilitating the exchange of data and services.
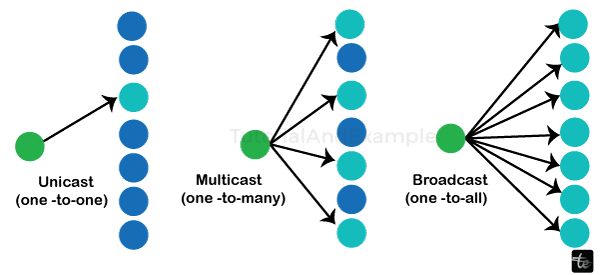
Communication Methods/Modes of Computer Network
To convey data and enable communication between devices, computer networks employ a variety of communication techniques. The main three are given as:
- Uni-Cast
- Broadcast
- Multicast
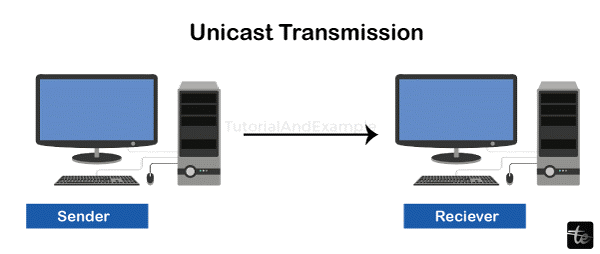
1.Uni-cast
In computer networks, the term "uni-cast" refers to a communication technique where data is delivered from a single source device to a particular destination device.
In point-to-point communication, known as uni-cast, only one source device sends data to one particular destination device.

Each data packet is addressed to a specific recipient because it is a one-to-one communication mechanism.
Targeted data transmission is made possible via uni-cast, which makes sure that only the intended receiver will receive the transmitted data.
Addressing:
The Internet Protocol (IP) is primarily used to implement uni-cast communication.
Uni-cast data packets are addressed using IP addresses, which are used to uniquely identify devices on a network.
Direct communication between devices is made possible by the assignment of a different IP address to each device taking part in uni-cast communication.
Transmission Technique:
Data packets are encapsulated during a uni-cast transmission by the source device and addressed to the IP address of the destination device.
The packets are forwarded by network devices (such as routers) using IP routing tables after being sent onto the network by the source device.
To identify the following hop in the transmission chain, intermediate network devices examine the destination IP address in the packet header.
The packets are delivered to the destination device, which then processes the data inside.
Applications:
For a variety of communication situations, such as visiting websites, sending emails, transferring files, and streaming live video, uni-cast is frequently utilized.
- Web browsing: A user's device makes uni-cast requests to a web server when they view a website, and the web server responds by sending uni-cast data packets containing the requested web content.
- Email transmission: To transfer emails from a sender's device to a recipient's device or email server, utilize uni-cast.
- Online gaming: Data packets are delivered directly between participants' devices in online gaming, where uni-cast is frequently used. This guarantee synchronized gameplay, real-time communication, and lowers network latency.
Advantages:
- Deliveries that are targeted: Uni-cast makes sure that data is sent to a particular destination device. The sender and the intended receiver can communicate privately and individually thanks to this customized delivery.
- Point-to-Point Communication: Direct point-to-point communication between devices is made possible via uni-cast. In order to guarantee that the communication stays private and limited to the two participating devices, it creates a dedicated connection between the source and destination.
- Data Privacy: Compared to other communication techniques like multicast or broadcast, uni-cast communication offers a better level of data privacy. The likelihood of undesired receivers accessing or intercepting the transmitted information is decreased because data is only sent to the designated destination.
- Reliability: Since uni-cast creates a direct link between the source and destination devices, it offers reliable communication. In order to reduce the likelihood of packet loss or interference, it makes sure that data packets are routed straight to the recipient.
- Flexibility: Uni-cast is capable of adjusting to various network topological and conditions.
- Network addressing: Uni-cast makes use of IP addressing, which enables effective data packet forwarding and routing across networks. A scalable and standardized approach for uniquely identifying devices and sending data to specific locations is provided by IP addressing.
Drawbacks:
While using Uni-cast communication in computer networks has a number of benefits, it also has significant disadvantages. Here are a few negative aspects of uni-cast:
- Network Scalability: When the number of recipients dramatically rises, uni-cast may become ineffective. Uni-cast requires that every packet be sent individually to every receiver, which increases network overhead as the number of recipients rises. This may affect the scalability and performance of the network.
- Consumption of Bandwidth: Each transmission in uni-cast communication needs its own allocated bandwidth. Uni-cast can use a significant quantity of network capacity in situations where a lot of data needs to be broadcasted to several receivers at once. This may result in network sluggishness and decreased overall network effectiveness.
- Network strain: Since each recipient need a unique data packet to be created and transmitted, uni-cast creates a greater strain on the source device. This additional strain may have an effect on the source device's performance, especially when numerous simultaneous uni-cast transmissions are necessary.
- Complexity of Addressing: Uni-cast uses individual IP addresses to identify and address each device. Managing and allocating distinct IP addresses to each device can be difficult and need careful network administration as networks get bigger and more complicated.
- Lack of Broadcast Benefits: Uni-cast communication does not offer the built-in advantages of broadcasting. Without addressing each recipient specifically, a single message cannot be sent through uni-cast to all devices connected to a network. This can be a drawback in circumstances where broadcast-style communication is necessary.
- Reliability Dependency: For uni-cast communication to work, the destination device, network infrastructure, and source device must all be accessible and in good working order. Communication breakdown and packet loss may happen from any errors or disruptions along this chain.
When developing and putting into practice communication solutions for computer networks, it is crucial to take these disadvantages into account. Alternative communication techniques, like multicast or broadcast, may be more appropriate in situations where the restrictions of uni-cast become substantial.
2.Broadcast
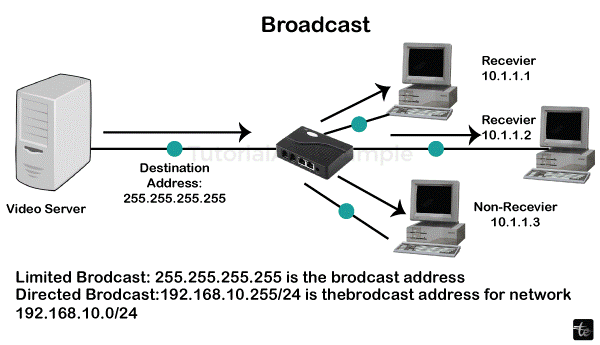
In computer networks, broadcasting describes the act of transmitting a message or packet to every device on a certain network or sub-net from a single source device. It is a basic communication technique used to provide information to numerous recipients at once.
A device that starts a broadcast transmits the message to the broadcast address, which is a specific address. The message can reach all devices connected to that network thanks to the broadcast address, which is normally the highest address in the network or sub-net. There are several uses for broadcasting in computer networks. To find the MAC addresses of devices on a local network, for instance, it is used by protocols like the Address Resolution Protocol (ARP).
A device can discover the MAC address related to a certain IP address by sending an ARP request.
In order to assign IP addresses and other network configuration parameters to client devices, Dynamic Host Configuration Protocol (DHCP) servers also rely on broadcasting. The required network configurations can be obtained by client devices thanks to the DHCP server's broadcast of a DHCP offer.
Additionally, network discovery methods like Bonjour or Zeroconf use broadcasting. These protocols enable automatic detection by other devices by using broadcast messages to proclaim the presence of services or devices on a network.
Even while broadcasting has its uses in local networks, it is crucial to manage and restrict broadcast traffic in bigger networks or when it crosses sub-nets. Broadcast messages may be filtered or restricted by routers and switches to limit excessive network traffic and potential security holes.
In conclusion, broadcasting allows for the simultaneous distribution of information to many recipients through computer networks, and it is essential for many network protocols and services like address resolution, network discovery, and device connection.
Applications:
There are several uses for broadcasting in computer networks, including facilitating communication and the spread of knowledge. Here are a few frequent uses:
- MAC addresses of devices on a local network are resolved using broadcasts by the Address Resolution Protocol (ARP). When a device just knows another device's IP address and needs to connect with it, it broadcasts an ARP message to the network asking for the MAC address associated with that IP address.
- IP addresses and other network setup settings are distributed to client devices by DHCP servers, which employ broadcasting. In order for client devices to receive the required network configurations, the server broadcasts DHCP offers.
- Protocols for network discovery like Bonjour or Zeroconf frequently use broadcasting. These protocols enable automated detection by other devices by using broadcast messages to proclaim the availability of services or devices on a network.
- WoL enables remote device activation. A WoL packet awakens a sleeping device from sleep or power-saving mode by broadcasting a message with the device's MAC address.
- Distributing audio or video streams over a network is done by broadcasting, which is utilized in multimedia applications. The streams are sent by streaming services or media servers as broadcast messages, which are concurrently received and played by a number of client devices.
- Network management systems frequently use broadcasting to convey orders, configuration changes, or status inquiries to several networked devices. This makes network infrastructure management and monitoring easier.
- Real-Time communication solutions like Voice over IP (VoIP) or video conferencing can utilize broadcasting. It makes it possible to send audio and visual data to several conference or chat participants.
- In situations requiring the distribution of an application or update to several devices connected to a network, broadcasting is used. Devices can receive and install the software concurrently by broadcasting the installation package.
Advantages:
Several benefits of broadcasting in computer networks support effective communication and information transmission. Here are a few significant benefits:
- Simple: Broadcasting makes it easier to broadcast a message or packet to several devices connected to a network. A single broadcast message can reach every device simultaneously rather than addressing each one individually. The complexity of addressing and targeting certain receivers is decreased by this simplicity.
- Efficiency: There is no need for numerous transmissions because broadcast messages are transmitted once and received by all networked devices. As a consequence, network congestion is decreased and bandwidth is utilized effectively. Broadcasting has the potential to conserve network resources and enhance overall network performance as compared to uni-cast (individual) transmissions.
- Scalability: The simultaneous distribution of information to many receivers makes broadcasting a highly scalable technology. It is especially helpful in situations where a network's large audience needs to get the same information, such network notifications or software upgrades.
- Saving time: By using broadcasting, devices no longer need to make separate information requests or queries. Instead, the information is simultaneously delivered to all devices. This saves time, particularly in scenarios when quick information delivery is essential, such as, in real-time communication or emergency notifications.
- Automatic Discovery: Network discovery protocols employ broadcasting, which enables devices to automatically find and recognize services or devices on the network. The setup and configuration of new devices are made easier by this automatic discovery, which encourages interoperability and simplicity of use.
Drawbacks:
A few disadvantages of broadcasting via computer networks include:
- Broadcasting can generate excessive traffic, which can slow down other network operations and affect their performance.
- Unauthorized devices may be able to intercept broadcast communications, putting sensitive data at risk and perhaps enabling harmful operations.
- Broadcast messages are delivered to any device connected to the network, including those that don't require the information, which results in wasteful data usage.
- Without additional infrastructure, broadcasting is often only able to reach devices within the local network.
- Excessive broadcast traffic makes it more difficult to pinpoint the precise devices that are creating network problems.
- Since broadcasting generates extra network traffic, it is inefficient for transmitting messages to particular devices.
- Since broadcasting is a one-to-all communication mode, it is not adaptable enough to target certain listeners or satisfy specific communication needs.
3. Multicast
A network communication technology called multi-casting makes it possible to efficiently distribute data to several receivers at once. It entails delivering data packets to a multicast group address, which the network infrastructure subsequently copies and forwards to all group members. This method reduces bandwidth usage and maximizes resource use, making it perfect for real-time collaboration, online gaming, and streaming video. Protocols like IGMP and MLD, which control and uphold multicast group membership, facilitate multi-casting. Data may be distributed across computer networks in a scalable and efficient manner thanks to multi-casting.
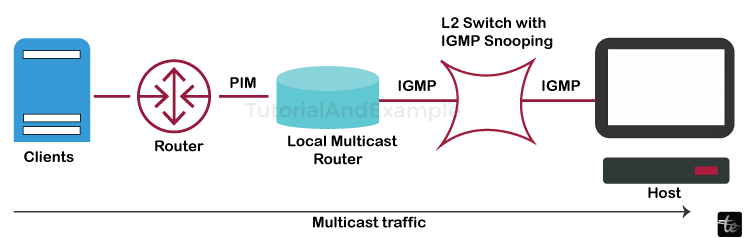
Applications:
There are several uses for multi-casting in computer networks, including simultaneous data dissemination to many receivers. Here are a few instances with clear explanations:
- Multi-casting aids in the effective delivery of the video stream to several viewers when you watch a live video or programme online. The movie is broadcast once to a multicast group rather than sending individual copies to each viewer in order to save network resources.
- Multi-casting enables the simultaneous distribution of software updates across a network to a number of computers and other devices. By doing this, network traffic is decreased and the update process is sped up.
- Multi-casting facilitates real-time communication between participants in multiplayer internet games. It enables synchronized gaming by enabling the game server to deliver game state information to every player participating in the same game session.
- Multi-casting enables teachers to distribute lectures or training materials to several pupils in various areas when it comes to distance learning. By ensuring effective and reliable content distribution, it lowers bandwidth needs.
- Multi-casting contributes to video conferencing by effectively distributing audio and video feeds to several participants. It makes real-time communication slick and synchronized possible.
Advantages:
- Multi-casting optimize resource utilization while preserving network bandwidth. Instead of sending data packets twice to each individual recipient, it sends them once to a multicast group. As a result, network congestion is decreased and overall network efficiency is increased.
- Data may be distributed scalable to a large number of receivers thanks to multi-casting. Multi-casting effectively reaches several devices or users without taxing the network infrastructure, whether it be for video streaming or software upgrades.
- Data transmission to numerous receivers concurrently is possible with multi-casting. This helps to ensure that everyone receives data simultaneously during real-time applications like online gaming or video conferencing, which improves user experience and cooperation.
- Multi-casting reduces the volume of network traffic as a whole. It reduces network strain and frees up network resources for other operations by distributing data packets to a multicast group rather than individually to each receiver.
- By maximizing resource utilization and lowering bandwidth needs, multi-casting decreases network expenses. It aids businesses in reducing infrastructure costs and makes content delivery effective without sacrificing quality possible.
Drawbacks:
Multi-casting in computer networks has a number of advantages, but it also has certain disadvantages. Here are the key disadvantages listed in easy-to-understand terms:
- Limited Network enable: Not all network devices or routers may enable multi-casting. The efficiency and range of multi-casting may be constrained in some network environments due to network equipment that is more dated or less technologically sophisticated that may not completely support multicast protocols.
- Implementation Difficulty: When compared to uni-cast or broadcast communication, multi-casting in computer networks might be more difficult to implement. It necessitates adequate transmitter and receiver device configuration, administration, and synchronization. It can be difficult to set up and maintain multicast group membership, especially in big networks.
- Lack of Reliable Delivery: Multi-casting does not provide reliable delivery to every member of the multicast group. This is in contrast to uni-cast communication, in which data is conveyed only to one receiver. Some recipients' ability to receive data consistently and with high quality may be impacted by network challenges like packet loss or congestion.
- Security issues: Multi-casting may provide security and privacy problems since data is concurrently delivered to several receivers. When dealing with sensitive or private material, it might be difficult to create secure communication within a multicast group. Additionally, unauthorized users could try to join multicast groups and get access to information they shouldn't have.
Difference between Uni-cast, Broadcast and Multicast:
| Communication type | Definition | Recipients | Deliver Method | Network Traffic |
| Uni-cast | Communication between a single sender and a single receiver. | One specific recipient identified by a unique address. | Point-to-point delivery. | Traffic generated only for the intended recipient. |
| Broadcast | Communication from a single sender to all devices within a network. | All devices within the network | Data is sent to all devices simultaneously. | Traffic generated for all devices within the network |
| Multicast | Communication for a single sender to a group of recipients. | A specific group of recipients identified by a multicast group address. | Data is sent once and received by multiple recipients within the group. | Traffic generated for the Multicast group only. |
Conclusion
In conclusion, the three unique computer network communication techniques are uni-cast, broadcast, and multicast. Uni-cast is the best option for one-to-one communication since it allows direct connection between a sender and a particular recipient. Data may be distributed through broadcast to every device connected to a network, making it easier to disseminate information but with the potential to clog up the network. Data is effectively sent by multicast to a specific group of users, saving resources and promoting scalability. Uni-cast is best for one-on-one communication, broadcast is good for mass communication, and multicast works well in one-to-many situations. It is easier to select the best communication strategy for certain network requirements when you are aware of the advantages and disadvantages of each communication technique.