How to Set Up a Home Network A 7-Step Guide
The prevalence of broadband connections in most households has enabled users to access the internet and necessary data or information through their internet service provider's customer premises equipment (CPE). Initially, this setup was largely satisfactory for meeting the needs of home networks. However, with the onset of the coronavirus pandemic, the landscape of internet usage underwent significant changes. As more individuals began working remotely and students shifted to online learning, the limitations of ISP's CPE capabilities became apparent. Many households found that their existing setups were inadequate to support the increased demands placed on their home networks. This shift in circumstances highlighted the necessity of improving home network performance, especially considering the essential nature of remote work and distance learning.
The trend towards network 'extensions', including the increased addition of various devices, especially smart home or automation devices, has also become common in recent times. The family PC was probably the only computer in the family several years ago. However, now, each family member could have a mobile device or two. Apart from this, the rest of the things that you will have with you, like computers, tablets, and phones, will be included, and you will also rely on the home network for connectivity.
Understand and implement the basic network setup by following this seven-step guide.
1. Evaluate home network hardware
When setting up a home network, consider the following hardware components:
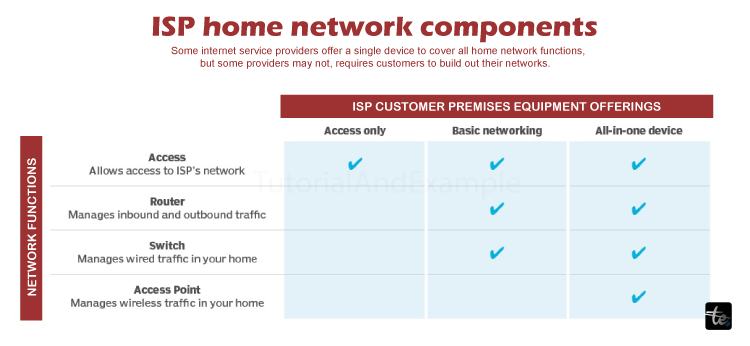
- The medium of the CPE is generally a computer cable or asymmetric DSL modem.
- A Router for redirecting traffic into and out of the network.
- To connect via wired and wireless clients, one just needs to switch to the wired section.
- A transmitter/receiver known as an access point (AP) permits the connecting of wireless clients.
Some ISPs will package the function of each device into one edge computing platform and are obviously going to charge more. Different vendors will have different approaches, which could be based on the network capability of the access device (only one device—no networking). Thus, the user is under the obligation to build out a networking system.
An ISP can create a multiple ways home network with cable or wireless equipment. The kind of products that an ISP has to offer, the setup complexity, and the number of devices that you want to connect all trigger a need to have extra equipment, which will allow you to extend access to additional devices.
 2. Weigh wired vs. wireless devices
2. Weigh wired vs. wireless devices
While cable devices provide more advantages in terms of performance and quality of service, they may require more money to purchase and tend to be less flexible than wireless devices. While it is possible to move wireless devices almost anywhere and use them, they might not deliver the expected excellent performance during video calls or handling large files or YouTube videos.
By their very specialty, wired devices include desktop computers, some stream media devices, DVRs/cable boxes, 4K TVs, etc. Ethernet is adopted to transmit data constitutionally among the devices where they will have RJ-45 connectors. Many electronic objects, such as computers, however, will be equipped with both wired and wireless networking options. If you are provided with one of the Internet connection methods, try to use a wired connection whenever it is possible, because you'll get the highest speed and a dependable connection.
Typical devices that use wireless technology include personal computers, tablets, mobile phones, some media streaming boxes, and smart devices for switching smart home components, including cameras, lights, doorbells, locks, and garage doors.
The common network for home users will be a hybrid infrastructure where wired and wireless gadgets coexist.
If you keep a notebook at the home office and rarely need to move, a wired connection (using an Ethernet cable) is recommended in this situation. While a wired connection remains the superior choice, adopting a USB Wi-Fi adapter could solve the problem of its older integrated adapter, noticeably resulting in better performance.
3. Connect wired client devices
For simple networking of the wired devices, it is a piece of cake. Use an RJ-45 network cable to plug the machine into the switch port or the ports on the router. Many routers are already supporting GigaEthernet (10001 mbps). In this case, if your devices may be Gigabit Ethernet as well, you can only achieve those speeds if you connect a Cat5e, Cat6, or Cat6a cable between the router and the device. It should be noted that the Cat5 cabling does not exceed the data transfer speed of 100 Mbps.
There is a certainty that Cat5e Ethernet cable can even run at gigabit speeds, but it can have performance problems with longer runs. So, Cat6 cable is more favorable because it can run at gigabit speeds, which are even further than Cat5e speeds. That is because Cat6a only recently became a standard, but most homes will only notice significant performance improvement if they have 10-gigabit devices.
These switches ensure that multiple wired units can be connected to a segment that is devoted to Ethernet. Disconnection or non-connection of one switch can lead to process disruption throughout in the house, and the connection of a number of wireless APs is possible to switches.
Operate are available at one being the managed or the unmanaged varieties. While unmanaged switching is cheaper than managed at first, it is usually more limited in terms of what it can do. Concerning this, they are often available in 5- or 8-port versions, and one can purchase such kinds of devices for just a few dollars per port. A managed switch is more expensive and user-friendly since it has various traffic-managing capabilities. Intelligent switches enable the realization of top-notch features like the creation of different virtual networks, segmenting of the traffic for particular clients, and blocking specific work clients from accessing the resources.
Some switches will have PoE (Power over Ethernet) capabilities to transmit power to the off-site device. In the case of connected devices such as APs or video security cameras, PoE can power these devices, and so if they need extra power ports, they will not be required since this is quite important in cases such as when these cameras must be in out-of-the-way places.
4. Connect wireless client devices
There is a requirement for Wi-Fi capability either from all-in-one ISP CPE or Wi-Fi AP once it is added to the clients. Make an extra effort to secure your Wi-Fi network by ensuring that it employs WPA2 password-protected access, preventing others from accessing your Wi-Fi network and any security compromises. Wi-Fi has different generations. Because of this, you have to get the latest version that your router supports, which most of the logical boards should already be on, or at least should have a very close set for best results. The way to make this handy if in case you need an update is using a USB adapter.
Wireless devices will work on two different wireless bands: In 2014, a report by the World Bank predicted that by the year 2030, 60% of the world's population will reside in urban areas. 40 GHz and 5 GHz -don't mix them up: 5G is a cellular, not Wi-Fi standard. 2. 4,00 GHz provides a lower level of bandwidth but treats devices that are several meters away better, hence making it strong in smart home devices. In contrast to 2. GHz, 5 GHz can support more bandwidth and have a larger throughput but the tradeoff for that is 5 GHz does not transmit as far when compared to 2. 4 GHz.
5. Extend home network range
Frequently, CPE contains a permanent camping pod in the common living area, such as a family room, which could make it far away from the workplace. The crucial consideration is whether the solutions for the CPE, router and Access Points (APs) are running well in the network when where one is determining the range. Your ISP must make sure that, apart from the performance of the router, CPE is also optimized. They should run speed tests online to verify the performance between a router and ISP.
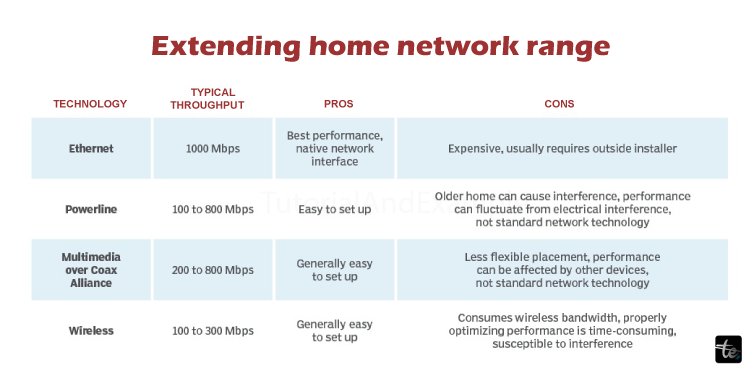
In the fourth stage, the "far away" spots of your house will be covered by more APs so that your house will not be the left-out one. This kind of connection involves using a wired Ethernet to connect your device to the internet, and this is the most likely way to go. Furthermore, the Ethernet can be reached wherever you have power in the house thanks to the powerline adapter -- which uses the wiring of your household -- with the Multimedia Over Coax Alliance cable or the cable TV line. The final possibility for achieving an extended Wi-Fi connection that we have at home is either using a wireless repeater, like AmpliFi, Eero or Linksys Velop.
 6. Protect your home network
6. Protect your home network
No matter if you have an ISP that you are using for routing or otherwise buying your router, securing your network is key when creating a home network must be the ultimate one. This entails, among others, user passwords setting on devices and changing all device passwords used for accessing or controlling access to the network.
Moreover, the router should also have a firewall turned on. A firewall allows carefully chosen traffic to pass and stops others from doing so.
Inside a router, the port may be used for different purposes of application. For instance, port 80 is utilized when accessing web traffic, and port 443 is used when you need to access secure web traffic. Furthermore, certain ports need to be opened in case of games or streaming devices usage. This way, you can limit the amount of ports that are allowed to be open through the firewall. This will make your life safer in the future.
For all these reasons, it is important to verify that any external access to your cable modem and router is shut down unless you really require resources to be accessed from outside the network. In accordance with that, developing a robust WPA2 password for every wireless input is a key factor in our network safety.
7. Optimize network performance
Lastly, for network creation concerns, this is about increasing the performance. Performance is measured in several different ways, including the following:
Bandwidth is any traffic that traverses the network in an envelope or capsule.
Latency, which is the time (measured in milliseconds) that the packet takes to reach the destination, is another aspect of the network quality.
Jitter would be the value of fluctuation in latency that jitters are in milliseconds.
Most speed tests that are network do typically surface these figures for you so that when testing and changing, you can validate if these changes are increasing your performance.
The lion's share of optimizing parameters will usually take place on the Wi-Fi side, which has more parameters to be assigned. House layout: Power may decrease depending on how the equipment is located, and doors, windows, or the like can create obstacles that can add up to interference.
Indeed, the channel that your neighbors are either now using and that you also must use so as to enhance your performance, also helps to achieve this task for 2. For the 4 GHz bands, it is better to use channels 1, 6, or 11 since these are the nonoverlapping ones. By selecting these three channels, you isolate the frequency breakups apart by half, and you thereby achieve higher capacity. As well as a viewer might infer the available frequencies to be channels 4 and 8 since no one is using them. Because of the space taken by the channels, they get deviated, and the result is interference that also affects channels 1, 6, and 11, which we all use.
After you’ve seized the infrastructure network, then is when you do the application optimization. The beginning of this process involves assigning traffic classes in your network, a process commonly initiated by inappropriate routers. QoS makes a distinction between different packets by providing a higher priority for a certain predefined type of packet than for others. As for this step, the traffic of video or VoIP can be scheduled to ensure that the voice or download packets do not interfere with the voice or video of online conferences. The way of setting QoS is different in every router; therefore, check your manual.