Reference Models in Computer Networks
Reference Models in Computer Networks
What is Reference Model
Reference models are used as a framework which is conceptual, and their purpose is to provide communicational paths among various heterogeneous networks.
In simple words, a reference model of computer networks could be defined as a layout, and its main purpose is to establish a model as to how communication should occur between users and devices.
The main purpose of developing and implementing a reference model is that it will be utilized in providing various standards and mechanisms for creating components of a network. It also plays an important role in implementing multi-vendor communication and its development.
Another main functionality or feature of a reference model is defining and promoting standardization. It is used to describe and authorize which functions are accessed to be performed at which levels.
Mainly, there are two reference models in computer networks. They are:
- OSI Reference Model
- TCP/IP Reference Model
Let us now understand the functionalities, features, working and implementations of the above-mentioned reference models in computer networks.
OSI Reference Model
Computer networks are being used by lots of users all around the globe. ISO (International Organization of Standardization) is responsible for the development or creation of the OSI model. The OSI model is also referred to as the ISO-OSI model.
OSI Reference model was the initial or first functional model for communications over the network.
The term OSI stands for Open System Interconnection.
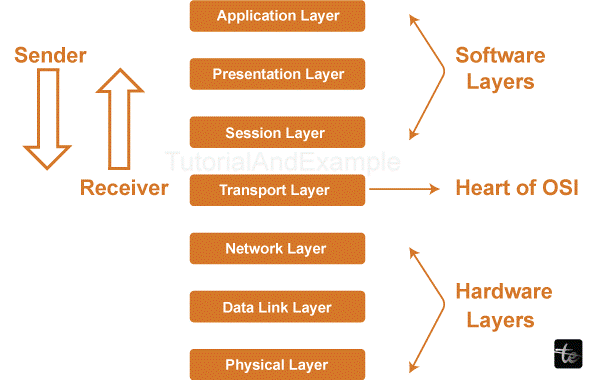
The architecture of the OSI reference model contains seven unique layers or levels. The seven layers of the OSI reference models are interconnected to each other in the architecture.
The layers of the OSI reference model are:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
Let us look at the working of these seven layers in a brief manner.
1.Physical Layer
The major functionality of the physical layer in the OSI reference model is to provide a connection between network nodes. The connector, electrical cable or a technology connecting the devices is defined by the physical layer. The physical layer is also responsible for the transfer or transmission of the data, which is in raw format. The raw data can be defined as 0s and 1s.
2.Data Link Layer
The main purpose of the data link layer in the OSI reference model is to establish and terminate a connection which was developed between two nodes which were physically connected on a network. The data link layer breaks the packets of information and converts them into frames. These frames are transmitted from the source to the destination. LLC (Logical Link Control) is used in the identification of network protocols and executes error detection mechanisms. MAC (Media Access Control) utilizes the MAC addresses and connects various devices, and provides access to transfer/receive data. LLC and MAC are the two parts of the Data Link Layer.
3.Network Layer
The network layer in the OSI reference model is use to perform two main operations. One of them is transforming segments into network packets by breaking them up and similarly reassembling the network packets into segments at the receiver's end. Another operation of the network layer in the OSI reference model is identifying the best path over a network and routing packets according to it. Internet protocol addresses are utilized by the network layer to route and transmit packets of data from the source to the destination node.
4.Transport Layer
The transport layer in the OSI reference model takes information or data from the session layer and breaks them into segments. This process is carried out on the receiver's end. Also, the transport layer is the component which will reassemble the broken-down segments and converts them into data. Another major function of the transport layer is that it is utilized to maintain the flow of control and transfer information or data by balancing the connection speed at the receiver's end. It also provides a mechanism for error detection and control and verifies whether the data transfer was successful or not. If not, retransmit it.
5.Session Layer
The session layer in the OSI reference model is utilized for the creation of channels for communication. These channels are also called sessions. The sessions are established and created between devices. The main purpose of the session layer is to create sessions, verify they are accessible and open until the data transmission occurs, and terminate them when the transmission ends. Also, the session layer sets checkpoints at the transfer of data. In case the session gets disrupted or an error occurs, the process can be traced and resumed from the checkpoint.
6.Presentation Layer
The presentation layer in the OSI reference model is used to create or prepare data and information for the application layer. The encoding of the devices is defined and carried out by the presentation layer. Also, the presentation layer compresses the data to make sure it can be safely received at the receiver's end. Any type of data and information transferred or transmitted by the application layer is accepted by the presentation layer, and it prepares it to be transmitted to the session layer.
7.Application Layer
The application layer in the OSI reference model is mainly utilized by the user's end software. The user's end software could be a web browser or email client. Various types of protocols which enable the transfer and receive protocols by the software are provided. There are various protocols of the application layer, and they are HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), DNS (Domain Name System), POP (Post Office Protocol) etc.
Let us look at the pros and cons of the OSI reference model over the years.
Pros of OSI Model
- The OSI reference model is considered to be a generic type of model. It also acts as a tool for guidance which can be utilized for the development of any network model.
- Another important advantage of the OSI reference model is that it is a layered model, meaning that it offers all the features where there is the minimum change between layers.
- There is another important advantage of the OSI reference model, which is, it can distinctly divide various types of services, interfaces, and protocols. This proves that the OSI reference model is flexible. Also, the protocols in every layer are easily replaced, and they are dependent on the network and its nature.
- The final advantage of the OSI reference model in computer networks is that it provides and supports both types of services; connection-oriented and connection-less services.
Cons of OSI Model
- One of the major disadvantages of the OSI reference model is that it is considered as a major theoretical model. Also, it does not utilize the usage and features of various technologies. Its real-time implementation is restricted by this con.
- Another major disadvantage or con of the OSI reference model in computer networks is its time of release or launching time. There were various TCP/IP protocols available when the OSI reference model was launched. This led to the ignorance of the OSI reference model by companies.
- One of the biggest cons or disadvantages of the OSI reference model is that it is considered to be very complex. Also, the implementation and the maintaining of it was considered to be very costly and time-consuming.
- Even though the OSI reference model consists of seven layers in its architecture, a few layers have fewer features and functionality in it. The layers are session and presentation layers. These layers have lesser operations and functionalities as compared to other layers in the OSI reference model.
- Another major disadvantage of the OSI reference model is that it fails to meet practical needs and is not as efficient and useful as TCP/IP reference model.
TCP/IP Reference Model
TCP is also known as Transmission Control Protocol. IP is also known as Internet Protocol. DoD (Department of Defence) was responsible for the successful creation of the TCP/IP reference model in the late 1960s. The TCP/IP reference model is purely based on standard protocols. IP is a similar version of another reference model, which is known as the OSI (Open System Interconnection) reference model.
As we learned previously, the OSI reference model contains seven layers in its architecture, whereas the TCP/IP reference model contains only four layers. In a few situations, the layers get incremented to five.
Features
- One of the major functionalities or operations of the TCP/IP reference model is to transmit data from a source point to a destination point. These source and destination points are of a computer.
- The main focus of the TCP/IP reference model is to make sure the data which is being transmitted from the source to the destination remains safe. Also, the receiver receives the same information or data.
- The data which needs to be transmitted will be broken down into smaller parts known as packets to achieve this functionality. On the successful transmission of packets from the source to the destination point, the packets will then be combined to gain the original data or information. Action is performed to maintain the integrity and accuracy of the information being transmitted.
TCP & IP
While TCP stands for Transmission Control Protocol, IP stands for Internet Protocol. Both TCP and IP are identified as two different protocols used in computer networks. The only difference between these two mechanisms lies in the transfer of the data or information. The main functionality of IP is to identify and track the mail and its destination. The main operation of TCP is to provide a safe transfer of data from the source point to the destination.
A similar type of protocol is known as UDP, which means User Datagram Protocol. UDP does not utilize the features and functionalities of the IP, unlike TCP, to establish a connection with other computers.
Working
For instance, a sample of data or information needs to be transmitted over the internet from a source point to a given destination point using the TCP/IP reference model; then, the TCP/IP reference model will initially break down or divide the given data into smaller parts known as packets. After the successful creation of packets, they will be transmitted over the internet to the destination point, and then the packets will be combined to gain the original information or data. This results in higher accuracy and security of the information as the transmission takes place through the internet.
The architecture of the TCP/IP reference model contains four layers and, in a few situations, five layers. Let us now discuss the layers of the TCP/IP reference model.
The layers of the TCP/IP reference model are:
- Application Layer
- Transport Layer
- Network/Internet Layer
- Data Link Layer
- Physical Layer
1.Physical Layer
The physical layer in the TCP/IP reference model can be defined as a set of defined applications which are used for the operations of network communications. The generation of data/information and requisition of connections is carried out by the physical layer in the TCP/IP reference model. The physical layer operates by the side of the sender or transmitter of the data.
2.Data Link Layer
The main function of the data link layer in the TCP/IP reference model is to identify the network protocol types of the packets. Other functionalities provided by the data link layer in the TCP/IP reference model are error detection, error prevention and framing. Ethernet IEEE 802.2 and PPP (Point-to-Point Protocol) are the two examples of protocols used in the data link layer.
3.Internet Layer
All available functions of the network layer of the OSI reference model are paralleled by the internet layer in TCP/IP reference model. In TCP/IP reference model, there are certain protocols whose main purpose is to carry out the logical transfer of information and data through the entire network. All those protocols are defined by the internet layer in the TCP/IP reference model.
A few of the protocols defined by the internet layer in the TCP/IP reference model are:
- IP: The full form of the term IP is Internet Protocol. Data will be divided into packets; the main purpose of IP is to carry out the transmission of those packets from the source point to the destination point by locating and verifying the IP addresses present in the headers of each packet. In TCP/IP reference model, the Internet Protocol has two major versions, and they are IPv4 and IPv6. Currently, all the major websites utilize the IPv4 version. Whereas the usage and implementation of IPv6 are increasing exponentially.
- ARP: The full form of ARP is Address Resolution Protocol. The purpose of using ARP is to locate the hardware address related to the host using a known IP address. There are various types of ARP, and they are Inverse ARP, Gratuitous ARP and Reverse ARP.
The Internet Protocol Suite contains the Internet layer in it. Internet protocol is mainly utilized in providing a group of protocols which are used in defining the Internet. The routing of data packets from a source point to a destination point is the primary function of the internet layer in the TCP/IP reference model. The main function of the internet layer is carried out by providing each device with a unique IP address. Using the unique IP address, the routing of the packets can be done easily by locating the IP address of the source and destination points.
4.Transport Layer
The transport layer in the TCP/IP reference model is used in providing protocols which are utilized in exchanging receipts of data acknowledgements. Also, another major function of the transport layer is to retransmit the packets which were declared as missing, and this is done to make sure that all the packets arrive in the same order at the destination point. Also, the transmission of the data packets from the source point to the destination point without any errors is another feature of the transport layer in the TCP/IP reference model.
There are mainly two protocols which are provided and utilized by the transport layer in the TCP/IP reference model. They are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
5.TCP (Transmission Control Protocol):
When two or more applications interact with one another, it is carried out by the usage of the Transmission Control Protocol. The Transmission Control Protocol follows a character-by-character rule while transmitting data instead of separate packets.
6. UDP (User Datagram Protocol)
User Datagram Protocol provides a datagram delivery service. In UDP, the verification of connections is not followed before and after the process. User Datagram Protocol is mainly used by applications that require the transmission of small amounts of data.
7. Application Layer
The application layer of the TCP/IP reference model is parallel to the transport layer of the OSI reference model. The main functionalities provided by the application layer in the TPC/IP reference model are end-to-end communication with other error detection and error prevention, along with the safe transmission of data from the source point to the destination point. The applications of the upper layers are shielded or protected by the data complexities.
There are mainly three protocols used in the application layer of the TCP/IP reference model. They are HTTP, HTTPS, SSH and NTP.
This was everything related to the Transmission Control Protocol/Internet Protocol reference model in the computer networks. This is the reference model which was derived from the functionalities of the Open System Interconnection reference model.