Double Spending On Blockchain
Blockchain: A list of blocks is a blockchain.
Every block has a hash and some information connected to it. These days, cryptocurrency is frequently employed in payments. It is a dispersed, distributed, and unchangeable ledger. Here's how blockchain technology operates. Let's say a user wishes to complete a purchase. You construct a block and share it with other people. After users approve the block, the payment is carried out. The users receive rewards when the block is introduced.
Recognizing Duplicate Expense
Blockchain is safe, but it continues to possess some vulnerabilities. Evil users or attackers exploit these weaknesses for their own purposes.
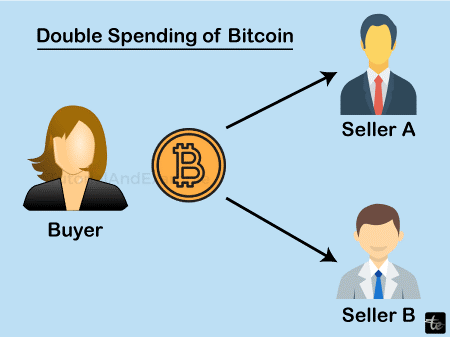
- The term "double spending" refers to using single electronic money to pay for multiple goods or services more than once. Users can duplicate money thanks to a technological bug.
- Someone with malicious intent can make several copies of an identical money file and use it in various places because digital dollars are nothing more than files.
- This problem may also arise if the network is altered or if just duplicates of the money are utilized instead of the original one.
- Additionally, double spends give attackers the ability to undo operations and make them happen twice.
- Through doing this, the customer pays money on both the initial block and the phony block that the attacker made.
- For the forged blocks which are verified and mined, the attacker also receives incentives.
What Causes Double Spending?
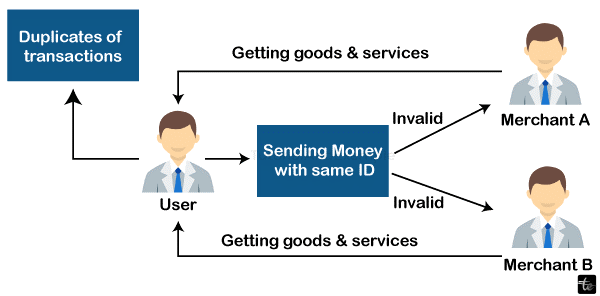
Physically, double spending is impossible. Transactions made via the Internet may encounter this issue. This usually happens when a third party cannot verify the transaction. It might also occur if the user has an unsecured wallet. Let's say a user wishes to use Merchants 'A' and 'B' for their services.
- The user and Merchant "A" engaged in an online transaction at first.
- On the user's computer is a copy of the currency.
- Thus, the user pays Merchant "B" with the same currency.
- Since the workers at the mine failed to verify the activities, both merchants now believe that the cash was actually refunded.
This instance involves paying twice.
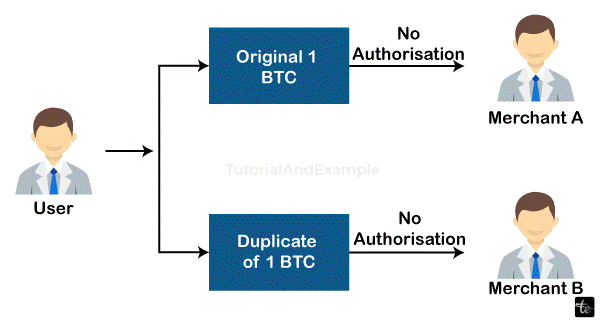
Let's say a user owns one Bitcoin. They wish to use both merchant A's and retailer B's services. The user versions and saves the same Bitcoin across several versions. In order to receive the service, the consumer has to send Seller A the original Bitcoin initially. The customer delivers Merchant B an additional copy of 1 BTC at the same time. The seller takes the Bitcoin and provides the service because additional miners didn't verify the second transfer. However, the sent cryptocurrency is not valid. This instance of double expenditure is this.
Many Forms of Double Spending Incidents
Different kinds of double-spending assaults exist.
- Finney Attack: One kind of double-spend strike is the Finney Attack. Here, a retailer consents to an illicit transaction. The hacker uses a solar eclipse attack to obscure the initial block. An illegal purchase is carried out. The real block then appears, and once more, the transaction is completed immediately for the actual block. The retailer thus suffers two losses of money.
- An attack known as a "race" occurs when two purchases are in competition with one another. The hacker uses two distinct computers to send an identical amount of money to two separate merchants. The vendors ship their merchandise, but the sales are rejected.
- 51% Attack: Small digital currencies are vulnerable to this kind of attack. Since hackers typically control 51% of bitcoin's mining power, they are free to do as they please.
Among the most widely used blockchains is Bitcoin. It employs a few security measures to discourage double-spending. In Bitcoin, there are two kinds of instances of doubling down on expenditure.
- The first instance involves creating counterfeit Bitcoin and distributing it to several recipients.
- In the second scenario, the transaction is completed, and once the service is received, the purchase is reversed.
There are steps taken in terms of security to address these fraudulent spending challenges. They are as follows:
- Validation: A maximum amount of nodes in a network validate events. A block is included in an inventory of outstanding transactions as soon as it is processed. Users submit block verification. Only the block gets placed on the public ledger if all verifications have been performed.
- Timestamped: Since the confirmed actions have a timestamped confirmation, they cannot be undone. When a payment in bitcoins takes place, it is completed and verified. However, the actions will be canceled if the exact same Bitcoin is used for additional purchases in the future.
- Block Confirmations: To ensure that there wasn't any instance of double spending, companies receive block verification.
- Retaining copies: Each node maintains a copy of every transaction, preventing the entire network from failing in the event of a failure.
To a great extent, these safety precautions have decreased double-spending. Let's talk about an in-depth illustration of how Bitcoin manages duplicate purchases.
- A user wishes to part with two bitcoins. The same currency can be made in multiple versions by them.
- The same cryptocurrency can be sent to two distinct discusses, such as "Bob" and "Alice," by the user.
- The two of them are added to the list of transactions that are pending.
- The confirmation method would be used to authorize the first transaction, T1.
- According to the verification system, transaction validation requires miners to complete at least six confirmations. The network now includes the block.
- Nevertheless, the confirmation mechanism would identify the second deal, T2, as invalid since it needed more confirmation. One block gets approved, and another gets turned down based on which block has the most confirmation. Thus, the transaction T1 is legitimate, and Alice got her bitcoin.
Methods to Avoid Spending Twice
Two strategies can be used to avoid double spending: Both autonomous and centralized
- Centralized Approach: In this instance, the transactions are verified by a secure third party. An outside organization can track every user's account. Assume that a user completes a purchase. The third-party uniquely identifies the deal. Subsequently, the transaction is validated and approved. The issue arises when we wish to transact business with nations wherein an intermediary is optional. Thus, decentralized structures are useful in these situations. Another disadvantage is that users won't be able to access the computer system if it fails altogether.
- Decentralized Approach: Bitcoin employs this strategy. The central government is not involved in this. Strong algorithms are used to verify each transaction. It turned out that the decentralized method was safer than the centralized one. Procedures are created, and each one performs its function at every stage.
How Can We Stop Spending Twice?
Because businesses are utilizing so many safety precautions, the incidence of double spending has significantly decreased. However, it is our duty as users to take a few steps to prevent these kinds of attacks.
- Before completing an additional transaction, a user ought to await at least six confirmations of the previous transaction. The more approvals from various users in the blockchain, the fewer double-spending attacks there will be.
- In order to prevent hackers from abusing their computer resources for personal gain, users ought to maintain them secure. Because physical is expensive, hackers frequently target the hardware component. They can change data or reverse every transaction if they manage to steal the hardware.
- To prevent needless malware attacks, consumers ought to eliminate spam emails and stay away from phishing. Hackers frequently use phishing schemes to obtain login information.
- Updates on a regular basis and the use of the most recent security programs are recommended. Bugs in out-of-date software have the potential to do serious harm.
How Effectively is Double Spending Managed?
The growing reliance on the blockchain has also made double spending assaults a significant issue. Numerous businesses have implemented safety measures.
- Features such as node verification of a transaction were recently implemented. The transaction must receive at least six confirmations in order to be approved.
- Once developed, the blocks cannot be altered. To ensure that nothing is undone, they have been rendered irrevocable.
- Every transaction is independently recorded by the network's distributed database of events. Every node in a network has an original of every transaction that takes place.
- Blockchain protocols ensure that every transaction is genuine in order to avoid double-spending. The hash idea is accepted. Every block has its hash in this case.
Blockchain's Drawbacks Regarding Double Spending
Regarding Double expenditure, blockchain has numerous drawbacks:
- Control of the blockchain: The main drawback is that if attackers are able to seize 51% of the processing power, they will have complete control over the distributed ledger and will be able to steal money from other users. Because transactions entail thousands of thousands of dollars, security is thus threatened.
- Information modification: Hackers can change transactional data. They can use attacks like the Twilight attack, Goldfinger attack, etc., to mine blocks while hiding the original blocks.
- Lack of body: The absence of a centralized body for verifying the actions taken is the third major issue. However, if businesses implement appropriate security measures and individuals are made aware of their homes, these issues will be resolved.