side-channel attack
Introduction
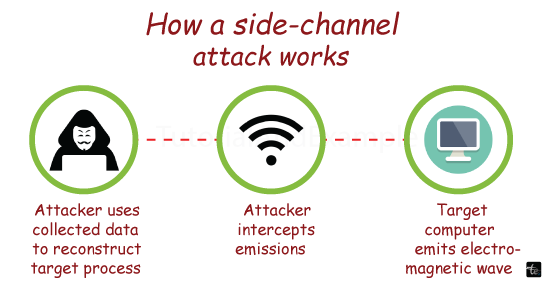
A side-channel attack is a type of security vulnerability that, instead of directly attacking a program or its code, measures or exploits indirect effects on a system or its hardware to obtain information about how a program is executed. Can be done or can be influenced. System. The most typical goal of these attacks is to accidentally measure hardware emissions in order to exfiltrate sensitive data, including cryptographic keys. Other names for a side-channel assault include sidebar attacks and implementation attacks.
To give you an example, let's say you're attempting to find out where someone has driven their vehicle. Following the vehicle or using a Global Positioning System (GPS) tracker would be conventional assault channels. In contrast, a side-channel attack would attempt to ascertain the car's use through measurements. Measuring variations in the car's weight, gas tank level, tire wear, paint scratches, and other factors, for instance, can provide insight into how the car has been used, where and how far it has been driven, and what is kept in the trunk—all of which can be done without having an impact on the vehicle or notifying the owner that they are being investigated.
Side-channel assaults, which were historically challenging, are becoming increasingly frequent due to a number of variables. Measurement equipment's increased sensitivity has made it possible to collect incredibly precise data on an operating system. Furthermore, attackers can now better comprehend the raw data they extract thanks to increased computational power and machine learning. Attackers can more effectively take advantage of minute modifications in a system thanks to their increased comprehension of the targeted systems.
High-value targets, including cryptographic keys, trusted platform module (TPM) chips, and secure processors, are also susceptible to attacks. A specific attack vector, such as a brute-force attack, can also benefit from partial information to increase its chances of success.
It can be difficult to protect against side-channel attacks. They may not change a system while it is operating, are hard to find in action, and frequently leave no trace. Even systems that have been physically isolated from other computers or networks and are considered air-gapped can be vulnerable to side-channel attacks. In cloud computing environments, where an attacker and a target share physical hardware, they can also be employed against virtual machines (VMs).
The history of side-channel attacks
World War II provides one of the earliest instances of a side-channel attack that we are aware of. At the time, Bell 131-B2 mixing devices were encrypting certain messages. When the machine stepped, causing one of the other rotors to rotate, a Bell Labs researcher observed that an electromagnetic spike could be seen on an oscilloscope, even from a distance inside the lab. He discovered after more investigation that he could extract the plaintext from the encrypted data by using these spikes.

Bell reported faced initial dismissal from the Signal Corps after reporting the problem. They deployed engineers to a facility across the street from the Signal Core cryptocenter in an effort to demonstrate the severity of the problem. He spent an hour recording encrypted signals coming from a distance of eighty feet from the cryptocenter. He deciphered 75% of the plaintext from these encrypted signals within a few hours.
This showed just how grave the threat was, and Bell Labs spent the next six months investigating the issue, as well as how it could be mitigated. Eventually, its engineers came to three potential approaches, which are still used today to counter side-channel attacks:
- Shielding: In this instance, obstructing the magnetic fields and radiation that were being released.
- filtering: adding electromagnetic radiation-stopping filters.
- Masking: using other transmissions to obscure the signals.
The machine's design was altered by the corporation, but the shielding and other adjustments led to problems with operation, and all of the current machines would have had to be shipped back to Bell Labs for retrofitting. Rather than using the updated version, the Signal Corps advised commanders to erect a 100-foot perimeter around their communications centers to thwart any attempts at interception using the newly discovered methods.
The issue was essentially overlooked until the CIA uncovered it in the middle of the 1950s. This time, the solution was to secure a 200-foot zone on both sides. To hide the signals, using many devices at once was an additional choice.
More countermeasures were tried in the years that followed, but new risks were also identified. Researchers discovered that information that may be utilized to decrypt information could also be revealed by voltage fluctuations, vibrations, and auditory emanations. The intelligence community code-named these attacks as TEMPEST.
With the intention of creating a set of guidelines to lessen the dangers associated with side-channel assaults, a variety of classified TEMPEST standards were created over time.
Van Eck phreaking is the term given to these eavesdropping techniques since Wim van Eck was the first to publish these dangers in an unclassified manner in 1985. Although the intelligence community was already aware of these threats, it was believed that nation-states were the only ones who could launch such attacks.
van Eck demonstrated that the attack was easily replicable by other parties by demonstrating that he could carry out his eavesdropping with only $15 worth of supplies and a TV. Details of several such low-cost monitoring methods were published in 2003 by Marus Kuhn.
The UK's MI5 was also experimenting with side-channel assaults in the same period that the TEMPEST attacks were being studied. Scientist Peter Wright of MI5 describes in his memoirs the agency's efforts to crack Egyptian codes in the midst of the Suez Crisis.
MI5 placed microphones close to the Egyptian embassy's encryption machine, and they would listen to the noises of the machine being reset every morning. They were able to interpret the coded signals by using the clues these noises provided about the changed settings. Acoustic cryptanalysis is the term used to describe this kind of side-channel attack.
Paul Kocher advanced side-channel attack technology during the 1990s. His 1996 paper demonstrated timed attacks that might defeat DSA, RSA, and Diffie-Hellman implementations. In addition, he was a member of the group that created differential power analysis, a new kind of side-channel attack. He not only invented a number of these attacks but also contributed significantly to the development of certain defence strategies.
Types of side-channel attacks
Side-channel assaults can be carried out by malevolent actors in a variety of ways, such as the following.
Electromagnetic
In order to reconstitute the internal signals of a target device, an attacker detects the electromagnetic radiation, or radio waves, that the target device emits. Electromagnetic side-channel attacks were the first. The Tempest technology of the National Security Agency (NSA) and van Eck phreaking could reconstitute a computer screen in its entirety. Modern side-channel attacks concentrate on monitoring a system's cryptographic functions in an attempt to extract secret keys. The entry barrier for electromagnetic attackers has been reduced by software-defined radio (SDR) devices, which enable penetration through walls and without physical touch with the target device.
Acoustics
The attacker measures the sounds generated by a device. It has been possible to recreate a user's keystrokes from an audio recording of them typing thanks to proof-of-concept (POC) attacks. Additionally, hackers are able to gather some information by listening to the noises that electronic components make.
Power
A hacker monitors or modifies a device's or subsystem's power usage. An attacker can determine the activity of a system by keeping an eye on the quantity and timing of power used by the system or one of its component parts. Some attacks, like Plundervolt attacks, may cut or lower power to make a system behave in a way that is advantageous to the attacker.
Optical
An attacker can learn more about a system by observing its visual clues. Some proof-of-concept (POC) attacks, in which audio is reconstructed from a video recording of an object vibrating in response to sounds, have been carried out, albeit infrequently against computers. Basic attacks involving shoulder surfing might also be included in this group.
Timing
A bad actor uses the length of time an operation takes to gain information. The total time can reveal information about a system's condition or the kind of process it is now doing. Here, the attacker can make precise predictions by comparing the victim system's lifespan to that of a known system.
cache memory
Memory caching is abused by an attacker to obtain more access. Pre-fetching and data caching are used by modern systems to increase performance. These systems can be abused by an attacker to gain access to data that ought to be restricted. This channel was used by the Spectre and Meltdown vulnerabilities, which mostly affected Intel processors.
Hardware weaknesses
Hackers may take advantage of data remanence—data that remains after deletion—or influence behaviour by manipulating a system's physical properties. Row hammering attacks occur when an attacker rapidly flips, or hammers, another nearby piece of memory on the physical random-access memory (RAM) chip in order to alter a confined area of memory. Memory with error correcting codes (ECCs) can aid in thwarting this assault. In a cold boot attack, the attacker rapidly drops the RAM's temperature, allowing some data to be saved after the power is turned off and retrieved back by the attacker.
Ways to prevent against side-channel attacks
A few best practice mitigations that organizations can put into place could help shield them from side-channel attacks. Because these assaults typically require very precise, in-depth knowledge of a system to be carried out, a company should treat information about vendors and implementation as a trade secret.
A few attacks that rely on memory or caches can be stopped by using address space layout randomization (ASLR). Using equipment designed for businesses can also aid in preventing system exploitation. Restrictions on physical access to systems are also necessary. Power conditioning devices can protect against power attacks, and businesses can store sensitive systems in Faraday cages that are isolated from outside interference.
Increasing a system's noise level is an extreme mitigation that will make it harder for an attacker to obtain valuable information. Moreover, even though these suggestions are usually inefficient and not advised, they might work in certain situations.
Firstly, in order to conceal which cryptographic process the attacker might be interested in, some systems will concurrently carry out a large number of irrelevant and similar operations. In addition, a system may launch superfluous components or processes to conceal its computing load and make it appear unrelated to its intended usage. Activating an extra electromagnetic radiation source could further conceal radio signals from potential attackers. Additionally, users have the option to match the colour of the text backdrop and font to make it difficult to reconstruct using van Eck phreaking or casual shoulder surfing.
Conclusion
Side-channel attacks underscore the critical necessity for robust countermeasures in cryptographic systems and secure hardware design. These attacks exploit unintended information leaks, emphasizing the imperative of fortifying defenses to safeguard sensitive data from compromise.