Reverse engineering in cyber security
Introduction
Most probably, everyone has heard about engineering as "an act or work of creation to simplify day-to-day work," and a person who does it is called an engineer who thinks and works with scientific methods and offers a technical solution to the need of people & society and solutions to problems.
Engineering is the act of developing such tools that ease human life. In a deep study of engineering, we came across two terms: forward engineering and back engineering. Now what are these:
“Forward engineering is the development of the application or high-level model with the given requirement including scratch or low-level information."
"Backward engineering is reverse of it, as here all the detailed information is collected from the existing application and system or device, it is also known as Reverse Engineering."
For example: When a machine is created/ made by an engineer is called forward engineering, and when the device/machine gets older, when its parts malfunction or break down completely, then its component are replaced, not the whole device. This is called reverse engineering.
Definition
“Reverse engineering is a process in which a product is deconstructed to extract design information including machines, aircrafts, software, architectural structure and many more or a method of deconstructing individual component of large components.”
Reverse engineering details how a machine is designed, using what components, and with what process so that it can be recreated. In cyber security, reverse engineering plays an important role as it helps to find out each detail of the threat, how, when, and why, and from which device it is created or shot to harm people.
In the computer world, reverse engineering is used for many purposes:
- As a way to make new products
- As a learning tool
- Preparing cheaper products compared to what's currently on the market
- Bridge data between different databases or operating system
- To uncover the undocumented features of commercial products
Traditionally reverse engineering was developed to apply to physical objects, but with the emerging time of computers, companies can use this process on codes for various applications. Companies probably use reverse engineering methods to create a replacement part for an obsolete product. For threats, system/ device, application, and network protection, backward engineering are used in which engineers can mimic a design without the original blueprint. The information collected from this process helps a company to teach their employees how things work and gives them a competitive advantage over others.
Examples of reverse engineering
- Computer parts: Reverse engineering is used to understand the computer's design and parts. The system and its parts are deconstructed by the engineer to replace old parts with new ones or run a test on a broken part. It is necessary for those who want to build computers.
- Network security assessment: Network security is equally a major concern for the companies for this reverse engineering is used by them to do network assessment for which they divide their team into two parts. They can be named red or blue teams, where one stimulates and monitors the attack. Here is a reverse engineering study about the attack to strengthen the security of a corporate network.
- Construction: Reverse engineering is mostly used in the construction industry as architecture can solve the design-related issues of a building. Using scanners, the engineer creates a 3D building design to study design flaws and fix them according to the information.
- Software: Software is also a good example of reverse engineering as it is required to maintain and improve the software simultaneously. By using the software, engineers extract the codes or parts of the software and analyze them to understand their functionality and use. It also helps in finding the application's loopholes and weaknesses and preventing them from exploitation by hackers.
- Mechanical project: In mechanical engineering, reverse engineering is used on different products like vehicles, air conditioners, washing machines, cars, etc. in this model, the machine is not created; instead, its non-functioning parts are disassembled. After finding a solution or fixing malfunctioning, these parts are assembled again to rebuild the products.
Benefits or advantages of reverse engineering
- Utilize in recreating a product
Recreating a product without any blueprint is the major goal of reverse engineering. With this method, companies can create a new and expensive version of an old and outdated product or software, an obsolete machine part, and a competitor's product.
- In repairing the existing products
Using this reversing engineering technique, engineers repair an existing product by identifying common design errors and learning to fix them for future products. Companies repair products under the maintenance scheme to improve their services and quality.
- To explore an existing product.
Engineer uses this reverse engineering technique to study and explore the product thoroughly. Evaluation of product is necessary for increasing the product growth and quality in the market & result in discoveries & innovation.
- An inspiring innovation
Reverse engineering opens the door to innovations as engineers study products and takes all the previous knowledge, which is important to develop innovative ideas.
- To discover vulnerabilities of product.
To detect product vulnerabilities, engineers use backward engineering by learning about the products in new ways. To keep up the product value in the market, it is necessary to regularly find the product's vulnerabilities.
- Conducting failure analysis
Backward engineering is used in analyzing the product failure, i.e., why a product did not work as intended. Product damaged parts should be analyzed to repair them to create a well-maintained product.
- To reduce the development cost of the product.
Timely analyzing the product helps them sustain market competition and understand how a competitor manufactures a product. By using reverse engineering, a company can develop cheaper alternative solutions.
Reverse engineering is used in the following industries
| Automobile industry Developing replacement parts To digitalized parts of old vehicle models It is used to deeply study and understand the issues and problems with existing automobiles. Used for analyzing and studying the competitors | Aerospace industry This technique is used for manufacturing the aerospace tools For conducting aerodynamic analysis For maintaining and developing parts of aircraft It is used for enhancing, adding, and fixing aircraft component. | Consumer goods industry In the consumer goods industry, reverse engineering is used to test and validate the conceptual design of products Helpful in developing product prototypes For analyzing competitor's product & for documenting different design iterations | Computer or cyber world To detect the reason for vulnerability. Study the software, device, application, or network to increase their efficiency &quality For secure digitization all over the world To analyze, detect, implement and repair tools and techniques. |
Steps for reverse engineering
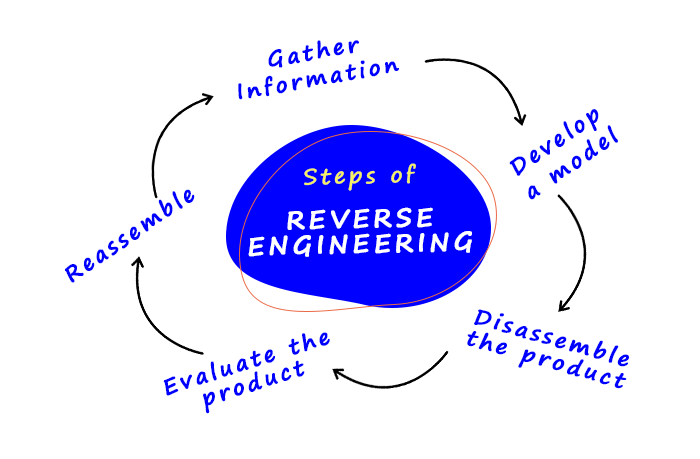
- Gather information
This is the first step in gathering information about the product, which includes measuring the product's dimension, understanding the device's coding, and identifying the source design. This step is essential for an engineer to learn everything about the product before deconstructing it. - Develop a model
After learning everything about the product, the engineer creates a sketch or model of it. These three-dimensional models are created using CAD- computer-aided design because it makes them analyze every part of the product by viewing an accurate presentation. By making this, the purpose of the product design is understandable.
- Disassemble the product
After these two steps, it's time to disassemble every part of the product because now they have an evaluated design model. Engineers disassemble the product or software layer by layer to know its weaknesses and vulnerabilities. To reassemble, the engineer organizes the product in parts to dismantle it. Each dismantled or removed part is analyzed, measured, or scanned to determine product functionality and use.
- Evaluate the product
The product is evaluated after carefully disassembling its parts to study them closely. In this evaluation, step engineers try to understand the errors and fix them to improve the product's quality. They also document the evaluation results or findings so that tracing scans be scanned to rebuild the product in the future.
- Reassemble
the last but essential step of reverse engineering aims to rebuild the product, which can proceed by reassembling the product. The rebuilding process evaluates or tests the engineer's knowledge and expertise in fixing the problem or making new changes to the product to improve its performance. In this reassembling process, the engineer again gets to learn how to create a product in detail. They named it a new or updated version of the product.
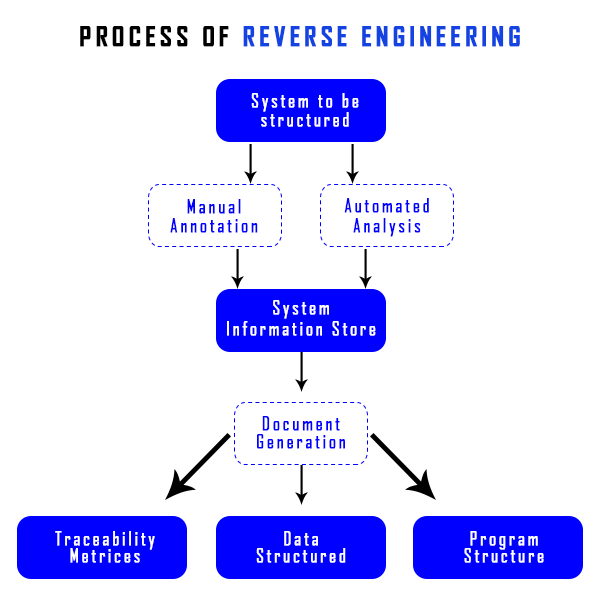
The detailed process of reverse engineerin
Above, we have discussed the reverse engineering process. In computers, this process is executed to find the footprint of the attacker and weakness points o the system that attackers can exploit. It follows certain steps in detail, such as:
- System to be structured
- Manual or automated analysis
- System information store
- Document generation
- Traceability metrics, data structure, and program structure use.
Principles of reverse engineering
- No need to mistake the hypothesis for the conclusion
The user or engineer yields hypotheses in reverse engineering, which can be done by understanding the application before reaching a firm conclusion. - Watch for a consistent style.
In reverse engineering, engineers always search for a consistent system design style. For example, databases are designed using a consistent strategy which should be necessary to understand for learning about the database. By using this, users can deduce the underlying strategy. - Expect odd constructs
Experts and database designers use uncommon constructs because users couldn't produce an accurate and complete database model (rather, this model never exists). - No need to be discouraged by the approximated results
In reverse engineering, only 80% of the data or information is captured by analyzing the parts very easily, but 20% remaining information is gathered by applying special techniques that detail the product or model. So an expert or user should not discourage from the approximate results in the first scanning of the product.
Technical risk of revere engineering
Different risks are associated with reverse engineering, and here we focus on the technical risk of reverse engineering: Confidential risk and integrity risk.
- Confidentiality risk - In reverse engineering, the confidentiality of information is the center point at great risk in it. In finding the attacker's footprinting, the confidentiality of information needs to be prevented.
- Integrity risk – In reverse engineering, parts of codes are
Tools used for reverse engineering
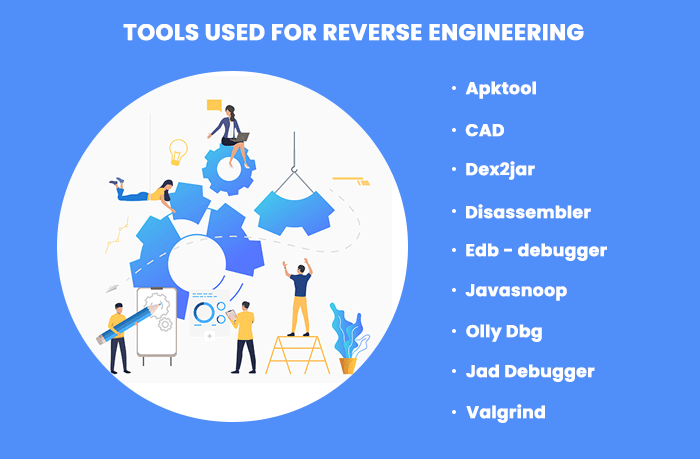
- CAD
An engineer uses the computer-aided designing tool to produce a 3D image of the product or the part of a product that requires re-manufacturing. They did this when the original blueprint of the product design was not available.
- Disassembler
To read the binary code of a software product disassembly tool, it displays the executable instruction as input. It generates textual files that include the assembly language code for the part of the program or the whole program. As stated, assembly language code is a textual mapping of the object code. Rather it is a single processor-specific process, but some of its versions or types can support multiple CPU architectures. To prevent this tool, a developer uses a debugging program. A disassembler of high quality is a key component in reversing method, and mostly built-in disassemblers are used, embedded in certain low-level debuggers. Some types of disassemblers are:- IDA Pro (Interactive disassembler)
- ideas ( Designed for the Microsoft Intermediate Language- MSIL)
- System monitoring tools
A system also has to go through reverse engineering because every communication in the cyber industry between a programmer and the outside world goes through the operating system, and to perform reverse engineering in a system, a variety of tools are required that monitor, sniff, explore and otherwise expose the program being reversed. These skillful tools display the gathered information about the application and its environment by the operating system. These tools are designed to do a detailed study about the system: connectivity with a network (monitor networking activity), registry access, file access, and many more activities such as exposing a program's use of operating system objects like pipes, events, mutexes, and so forth.
- Debuggers
A simple program code is too complex for a human to predict every single potential outcome. Every software developer uses a debugger to observe their program while running. Two important features of debuggers are:- They can set breakpoints
- Ability to trace through code (known as single stepping)
In a general scenario, a certain program has breakpoints that make the user select a certain code or function anywhere in the program and instruct the debugger to pause the program execution once that line is reached. The debugger stops when a program reaches the breakpoint and displays the program's current state. At this point, either debugger should be released, and the program will run continuously, or start tracing through the program. Debuggers trace the running program when running, where one line of code is executed and froze for some time, allowing the user to alter or observe the program's state. The further user executes the next line, and the process continues in repetition.
Debuggers are used by reverse engineers in disassembly mode as a built-in disassembler is used by the debugger to disassemble code on the fly. Some of the features of debuggers are as follows that are required for reverses:- Powerful disassembler
- Hardware & software breakpoints
- View of memory and registers
- Process information
- Some debugging tools are OllyDbg, IDA Pro, Numega SoftICE, etc.
- Decompilers
- One forward step from the disassembler is called a decompiler. Decompilers reverse the complication process by taking an executable binary file to produce readable high-level language code from it and obtain the source file. Therefore, these are known as the reverse's dream tool. Rather it is impossible to restore the original code in its exact form because the tracing process always removes some of the necessary or unnecessary from the program.
- Apktool
- This is a third-party tool used for reverse engineering an application or software. This tool can decode resources from the original form (including XML, 9.png files, resources. arsc) and can debug small code step by step & recreate them after making some adjustments. Due to its project-like file structure, it is easier to work with apps and does automation of tasks like building apk, etc.
- Dex2jar
- This tool is a lightweight application interface (AI similar to ASM) programmed to read Dalvik Executable format (.dex/.orex). With some features and components used to work with Android and Java. Class files. For example: modify an apk, DeObufuscate a jar. Some other components:
- Dex-ir = It is programmed to represent the dex instruction
- Dex-translator = Its job is to convert or translate the instruction, such as read dex instruction to dex ir format & after some format, convert them to ASM format.
- D2j-smali = Assemble from smali files and disassemble dex to smali files.
- Dex writer = To write instruction or code the same way as dex-reader.
- Edb-debugger
This debugger is programmed to perform modularity on the Linux equivalent to the “Olly debugger” on the window. Some of the features of the Edb debugger are:- Have intuitive GUI interface and basic instruction cycle
- Able to view/dump memory region
- Does the usual debussing operation such as step over/ step –into/ run/ break
- Have various plugins with debugging core to provide a drop-in replacement. Various debugging APIs are available on the given platform; the user has a plugin that implements any of them.
- Does the effective address inspection and also generation & importing of symbol maps
- The data dump view is tabbed, allowing several memory views to open simultaneously and quickly switch between them.
- Javasnoop
This aspect security tool is programmed to test the security of the java applications. It depicts how Aspect is leading the industry in providing verification services and not only for web applications. It works like a debugger that attaches an existing process and instantly begins tampering with method calls, looking at what's happening on the system and running custom code.
- OllyDbg
It is a debugging tool for Microsoft windows. It is a 32- bit assembler-level debugger tool that analyzes the binary code and makes it useful when source code is unavailable. Some of its features are as follows:- This tool has an intuitive user interface with no cryptic commands that directly load and debug DLLs.
- Ollydbg searches the whole allocated memory to find references to constant & address range and updates & shows fixups
- It also assembles commands into the shortest binary form
- Examine and modifies memory, set a breakpoint (conditional, memory, logging, and hardware breakpoints), and pause the program on-the-fly
- 3DNow, SSE, MMX data type and instruction (Athlon extension) and assembles commands into the shortest binary form
- It has an open architecture due to which many third parties can plugin
- It does the object file scanning that includes locating routines from object files and libraries
- The whole code (binary or text) is analyzed, including API calls, constants, switches, recognizes procedures, traces registers, loops, strings, and table
- This is unnecessary because it has no trash in the system registry or directories.
- Able to understand de-budding information in Borland format
- Provide comments, user-defined labels, and functions description
- It can be attached to the running program and debug the multithread application. After debugging, it can save patches between sessions and further write them back to executable files
- As it is a configurable disassembler, it supports both IDEAL and MASM format
- It has full UNICODE support and also recognizes UNICODE and ASCII strings
- It traces the program execution and log argument of known function and also recognizes the complex code construct (call to jump procedure)
- With the help of an external file. It provides context-sensitive help on API functions.
- Jad Debugger
Jad debugger is available in Kali Linux and reverses engineering, used for debugging java applications and other purposes. This tool is a command line utility Java decompiler written in C++. It provides a comfortable interface to the user for source browsing, project management, etc., because behind the scene, various graphical shells are executing this program.
- Valgrind
In reverse engineering, the Valgrind tool is used for debugging and profiling Linux programs, in which detailed profiling is performed to speed up the program's processes. It saves hours wasted in bug hunting by automatically identifying memory management and threading bugs, making the program more stable. This tool is used to build new tools & also includes six production-quality tools such as:
| Memcheck | A memory error detector |
| DRD and Helgrind | These are two thread error detector |
| cachegrind | It is a cache and branch-prediction profiler |
| callgrind | It is a branch prediction profiler and a call-graph generating cache |
| Massif | A heap profiler |
Some of the experimental tools are also included in it, such as:
| DHAT | It is a second heap profiler that examines how heap blocks are used |
| Scheck | It is a stack/ global array overrun detector |
| B | VB A pinpoint basic block vector generator |
Conclusion
Reverse engineering is a method or process in which a piece of hardware or software analyzes its functions and information flow to understand its behavior and functionality better.
In cyber security, it is used to create a defensive system or an unbreakable protection shield from cyber-attacks and criminals.
For example: In cyber defense, malware is commonly reversed engineered. Reverse engineering is also a means to sustain competition in the market. Some of it is considered a tool to grab detailed knowledge about the product, learn about the design's flaws and rework for the same.
Various reverse engineering tools are available in the market, provided by Kali Linux, which are already built-in and come out of the box with Kali Linux.