Firewall Architecture
Based on predefined security rules, the firewall allows only secured traffic and block unauthorized, malicious applications. A firewall is placed in the network to judge all the incoming packets and only allow secured packets.
Factors considered while architecting Firewall:
- The Ability of the particular organizations to implement firewall architecture.
- Decided budget of an organization on implementation of Firewall.
- Aims decided by the organization for network security.
Different implementations of Firewall architecture:
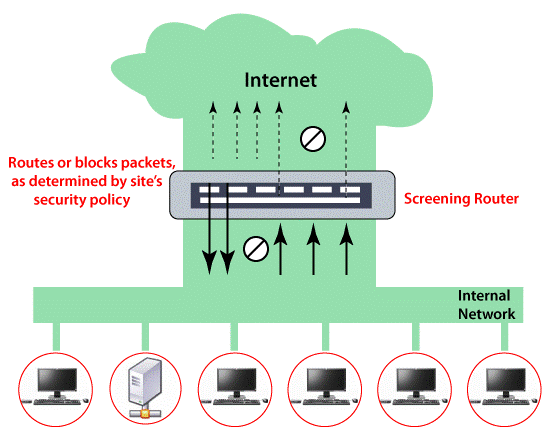
Screened Host Architecture:
It is the combination of packet filtering router and firewall methodology such as application proxy server. Before accessing system functionalities router filters all packets in traffic. Services are provided by the host attached to the internal network. The basic security is provided by packet filtering. Proxy operations are performed. It pre-screens the packets entering the system to minimize network traffic. It is responsible for reducing the load on the proxy server. Application proxy checks HTTP and other application layer protocols. This host is called a bastion host. It should be protected against attacks.
Characteristics of Screened Host Architecture:
- One Packet Filtering Router.
- One Bastion Host.
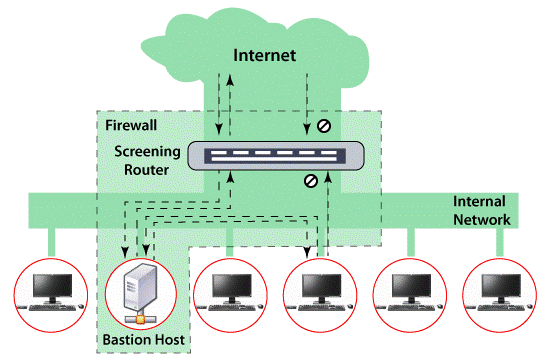
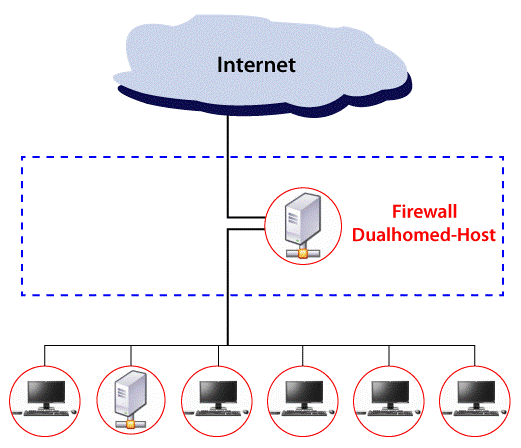
Dual-Homed Host Architecture:
The more complex version of Screened Host Architecture is Dual-Homed Host Architecture. To protect our system from unauthorized users accessing confidential information, Dual-Homed Host Architecture is used. It is the architecture involving the use of two network interface cards. Secured access is provided by Dual-Homed Host Architecture. Advance security is provided by configuring one NIC inside the network and another NIC in the external network. It is capable of routing one packet from one network to another network efficiently and securely. The server that provides secured access with firewall, gateways, and proxies is Dual-Homed Host Architecture. It provides a very high level of control by not allowing any of the packets from the external network if such a rule is specified by the user. External attacks are prevented with the help of Network Address Translation that is converting external IP address to internal IP address.
Characteristics of Dual-Homed Host Architecture:
- One Packet Filtering Router.
- More restrictive form of Screened Host Firewall.
- Dual-Homed Host Architecture supports a Bastion Host with two Network Interface Cards.
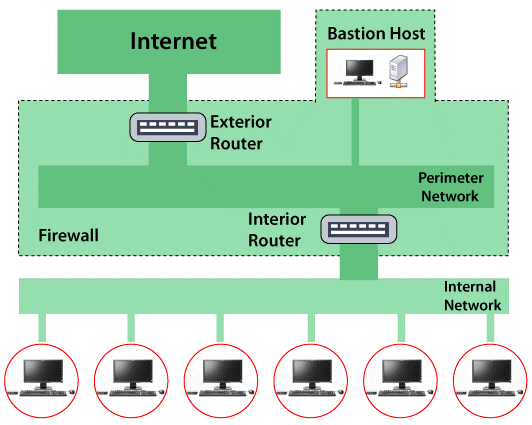
Screened Subnet Firewall:
Screened Subnet Firewall is the variation of the Dual-Homed Gateway and Screened Host Firewall. In order to get more flexibility and throughput different components of the firewall are maintained on separate systems. Screened Subnet Firewall is less complex as a separate component will perform separate task. It separates the internal network from the internet. Bastion hosts are more vulnerable. They are attacked despite tight security. If the attacker successfully attacks the bastion host, he/she can spoil the system security. Screened Subnet Firewall uses two screening routers for providing security. It is mainly used in e-commerce and financial systems. Its main use is to establish a Demilitarized Zone often called a DMZ. Screened Subnet Firewall is mainly used in the corporate network. Many high-traffic system working with high speed uses Screened Subnet Firewall. The architecture has two main components that are bastion host and a packet-filtering router. Each host is responsible for protecting the internal network. There exist different models of Screened Subnet Firewall. One of the models of Screened Subnet Firewall consists of Dual-Homed bastion host between two filtering routers. Three important components used in this architecture are:
The first component connects with the internet and it acts as a public interface.
Second component act as an intermediator between first and third component. It is the middle zone ( DMZ ).
The third component mainly works with the intranet.
Characteristics of Screened Subnet Firewall:
- Screened Subnet Firewall supports Two Packet Filtering Router.
- One Bastion Host.
Screening Router:
It works same like the Packet Filtering firewall methodology. It is responsible for checking all the incoming and outgoing traffic and according to predefined rules it routes the packets. It is cost-efficient. It can be used as perimeter protection for internal network. These are mainly useful for the internal Firewalls. It can be used in networks that are providing services to the Internet. Service Providers mainly use Screening router between the Internet and their service hosts. If the router is attacked, system security will come in danger.
Screening router Firewall architecture is a good choice for a situation where:
- The number of protocols used in the application are limited.
- The protocols used are straightforward.
- The network where there is a very high level of host security.
- There is a requirement for maximum security.
- You require Redundancy